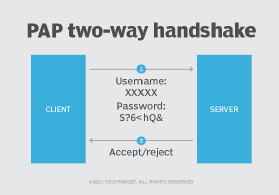
Pap Password Authentication Protocol Acronym Business Stock Vector (Royalty Free) 2018592065 | Shutterstock
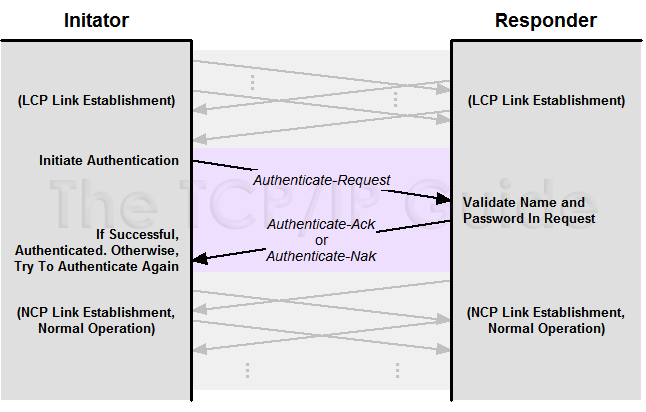
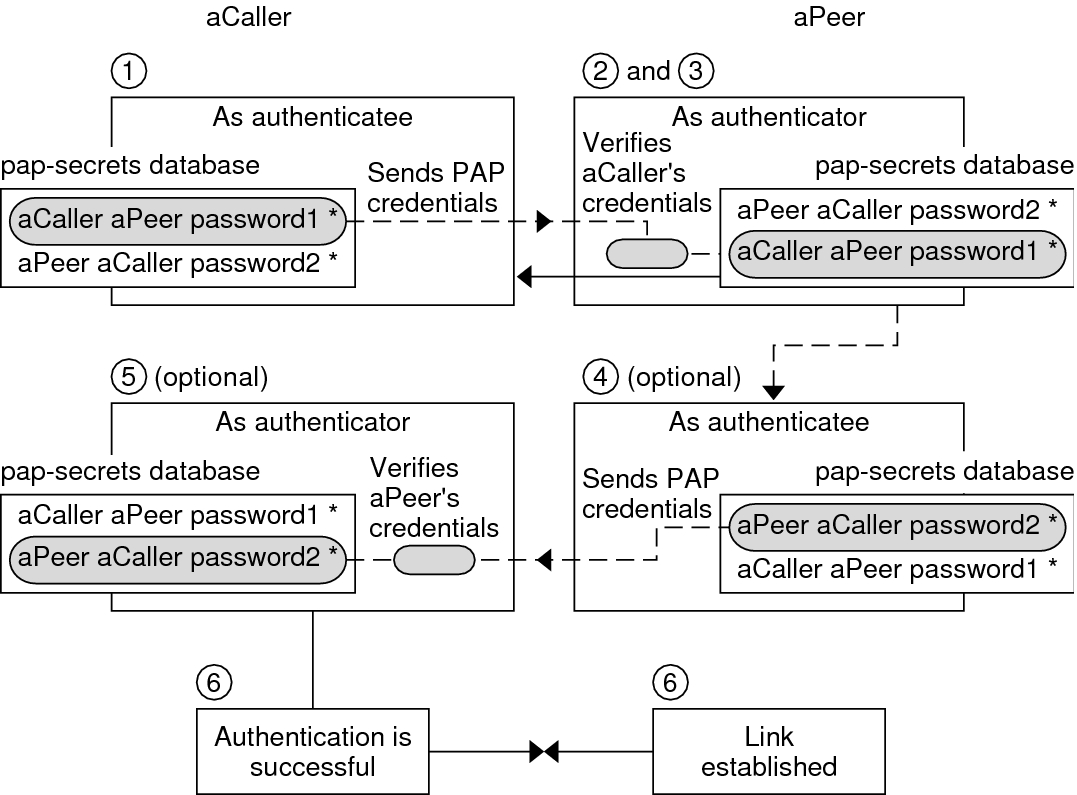
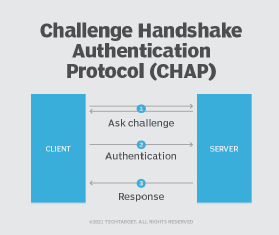
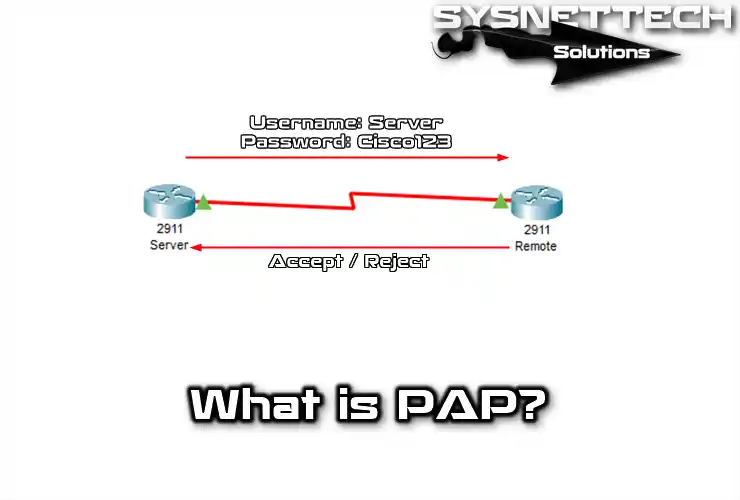
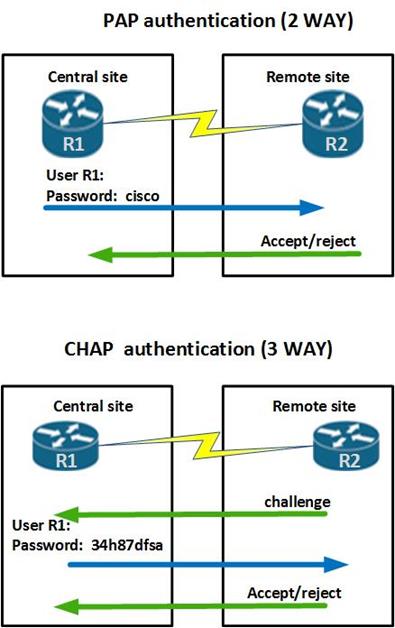
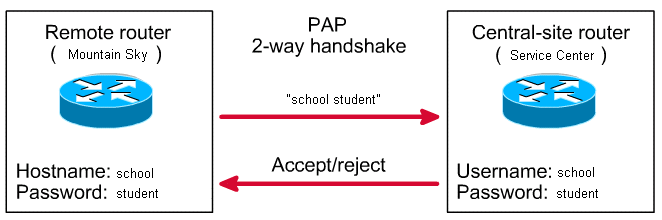
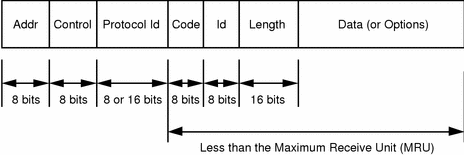
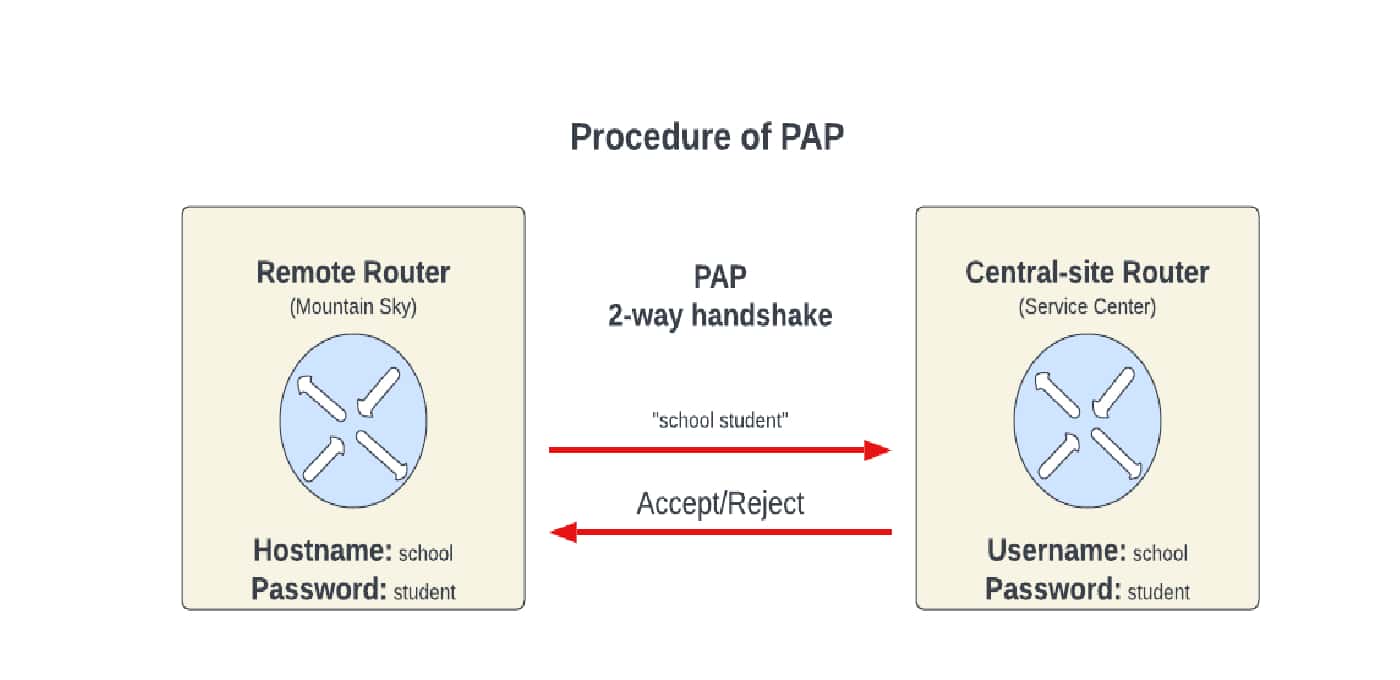
The TCP/IP Guide - PPP Authentication Protocols: Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP)
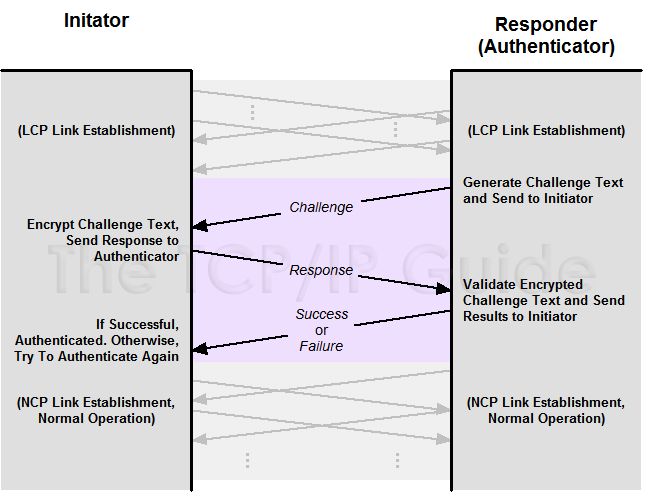
The TCP/IP Guide - PPP Authentication Protocols: Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP)